Is your Internet of Things (IoT) ecosystem as secure as you think? The increasing connectivity of our devices brings unprecedented convenience, but it also introduces significant vulnerabilities, making robust security measures for remote access absolutely critical.
Secure Shell (SSH), a cryptographic protocol designed to secure communications across untrusted networks, is the cornerstone of secure remote access, especially for the burgeoning world of IoT. Its widespread adoption stems from its ability to provide a secure tunnel for remote login and the execution of other secure network services. But, as the number of IoT devices explodes, ranging from smart home appliances to industrial sensors, the importance of securing the connections to these devices through SSH cannot be overstated.
Remote SSH login, in the context of IoT, typically serves three primary functions:
- Remote Monitoring and Management: Administrators can remotely monitor the performance and status of devices, ensuring optimal operation and swift troubleshooting.
- Configuration and Updates: SSH facilitates the remote configuration and deployment of software updates, essential for maintaining security and functionality across a fleet of devices.
- Troubleshooting: When issues arise, SSH allows for direct access to device logs and diagnostic tools, enabling IT professionals to swiftly identify and resolve problems without physical presence.
The implementation of these remote access methods comes with some serious considerations, the first step should always be ensuring that only authorized devices can establish an SSH connection to the IoT device. This is followed by, testing the SSH connection to make sure everything is working correctly.
To test the connection, open your preferred SSH client (e.g., PuTTY on Windows, or Terminal on macOS/Linux), enter the IP address of your IoT device, and provide your username and password (or SSH key) for authentication. After successful authentication, you can access and manage your IoT devices remotely, offering the flexibility to control your devices from anywhere with an internet connection.
The importance of strong password and authentication is always vital for a secure connection to enhance security, in modern world of IoT, the best practices for remote access are critical.
| Best Practices for Remote SSH Access in IoT | |
|---|---|
| Use a Dedicated SSH Client: | Employ a reliable SSH client like PuTTY (Windows) or Terminal (macOS/Linux) for managing connections. These clients offer features and security protocols to help you to securely connect. |
| Change the Default SSH Password: | One of the first steps to secure your SSH is to make sure you change the default password, for instance if you're using a Raspberry Pi, and the device has a default username and password, be sure to change it, as soon as possible. |
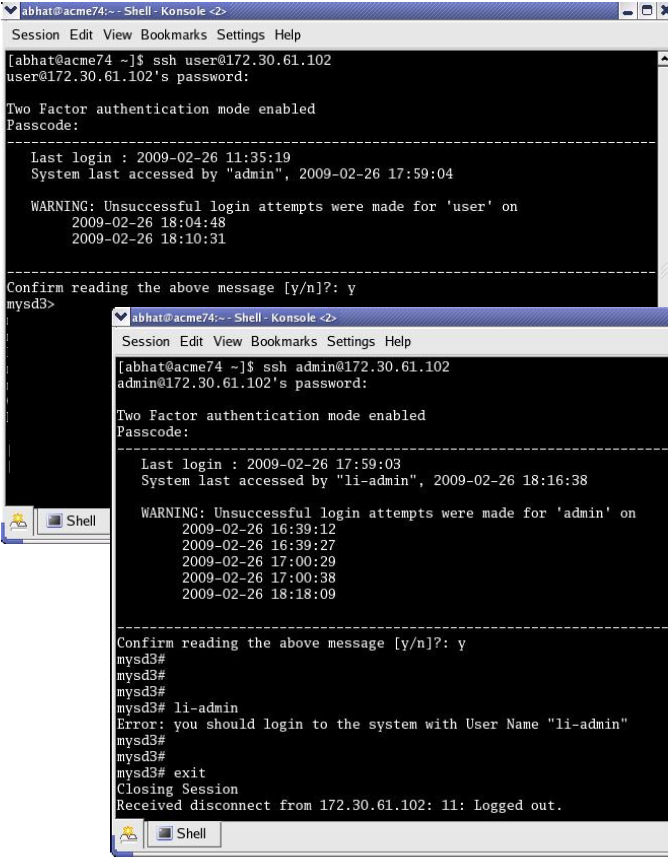
| Implement Two-Factor Authentication (2FA): | Using 2FA provides an extra layer of security. With 2FA, you not only need your password but also a verification code, typically from an authenticator app on your smartphone, to log in. |
| Restrict Access by IP Address: | Configure your IoT device to only accept SSH connections from specific IP addresses. This reduces the attack surface and prevents unauthorized access. |
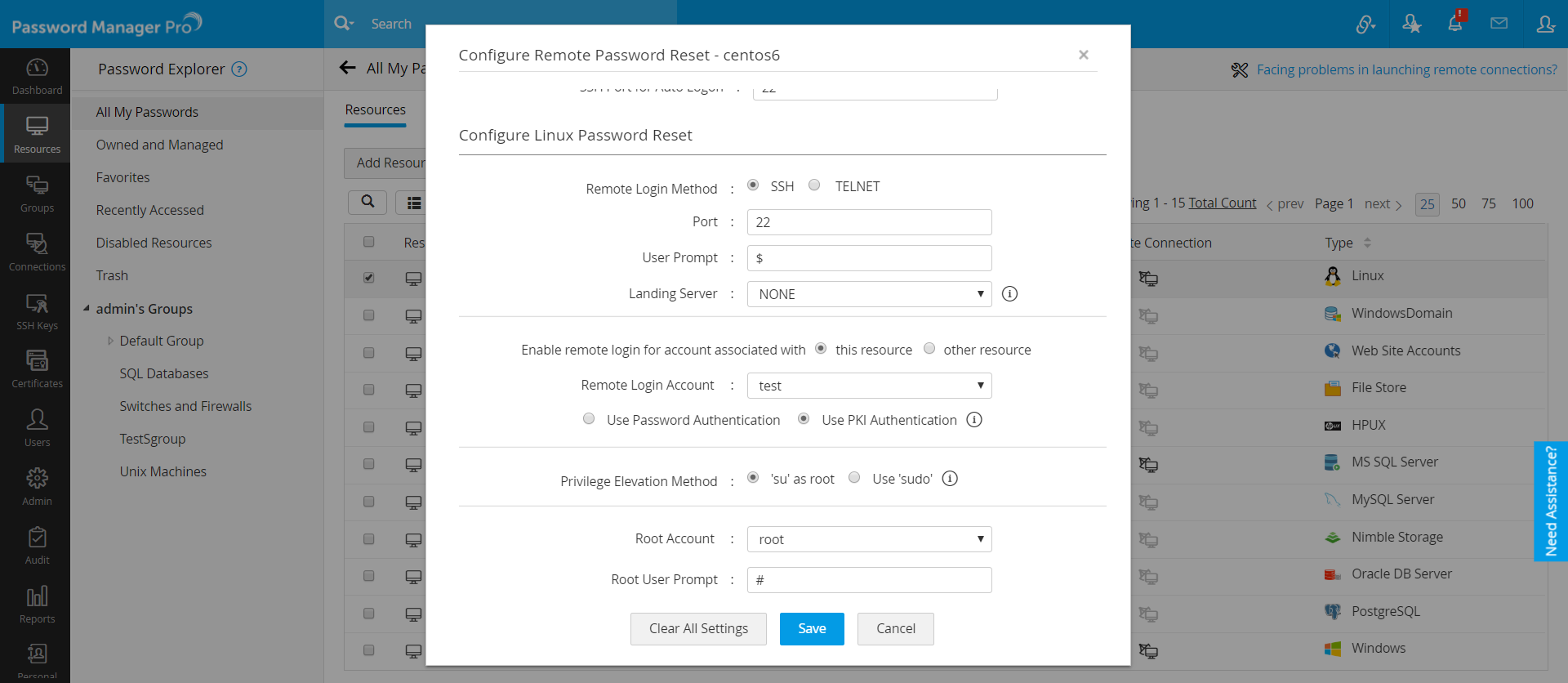
| Disable Password Authentication (Use SSH Keys): | Instead of using passwords, generate SSH keys for authentication. SSH keys are more secure than passwords and protect against brute-force attacks. |
| Keep Software Up to Date: | Regularly update the operating system and SSH server software on your IoT devices. Updates often include critical security patches. |
| Monitor Logs: | Regularly review SSH logs for suspicious activity, such as failed login attempts or unusual connections. This helps you identify potential security breaches. |
| Implement Intrusion Detection Systems (IDS): | Consider using an IDS to monitor network traffic for malicious activity and alert you to potential threats. |
| Use a Firewall: | Configure a firewall on your IoT device to control inbound and outbound traffic. This can help you to block unwanted connections. |
| Regular Security Audits: | Conduct periodic security audits to identify and address any vulnerabilities in your SSH configuration. |
Reference: Example.com/iot-ssh-security (Please Replace with an actual, authoritative source on IoT security).
For developers, IT professionals, and tech enthusiasts alike, the ability to securely connect to IoT gadgets via SSH significantly enhances productivity. With the rising prevalence of IoT in both personal and professional spheres, remote access and control become paramount.
Remote SSH login on platforms like Android simplifies troubleshooting, configuration, and monitoring of your IoT devices, eliminating the need for physical presence and conserving time and resources. Similarly, remote SSH login password management is crucial for both the security and efficiency of these devices. In a world where IoT devices are increasingly integrated into both private and professional environments, managing these devices requires strong password practices and security. The ever-expanding number of connected devices poses a challenge to the ability to maintain security and prevent unauthorized access.
By mastering remote SSH login and secure password practices, you significantly diminish the risk of unauthorized access, guaranteeing the integrity of your IoT infrastructure. As IoT ecosystems expand, the need for secure remote access grows more pronounced. Whether managing a single smart device or an entire network of industrial sensors, secure remote access is a necessity.
Implementing the `socketxp iot agent` and remote SSH access can further enhance your IoT security. First, download and install the socketxp iot agent on your IoT device. Then follow these steps:
Download and install the socketxp iot agent on your iot device from here.
Follow the setup instructions provided with the agent
Configure your SSH settings within the agent interface.
Connect and test your SSH connection.
Remote SSH login password management is not merely about convenience; it is fundamentally about safeguarding sensitive data and preserving operational integrity. IoT devices often reside in environments where physical access is limited or impractical, making remote access indispensable. However, this convenience introduces risks if weak passwords or poor security practices are in place. This emphasizes the need for robust password management and security procedures.
The focus should always be on managing remote SSH login iot passwords; it is a critical aspect to ensure the security and functionality of IoT devices. As the number of IoT devices continues to grow, ensuring secure access through SSH (Secure Shell) has become more important than ever. This highlights the best practices for remote SSH login, focusing on robust password management, implementing strong authentication protocols, and adhering to a set of stringent security policies. Restricting access to specific IP addresses or implementing IP-based login in the web browser can also fortify security. This approach virtually conceals the device from port scans and acts as a shield against DDoS attacks.
Ultimately, the best approach is to secure remote SSH login for IoT devices by embracing strong password authentication. This journey is all about achieving the highest security standards, protecting sensitive data, and ensuring the smooth operation of your IoT systems.