Is the security of your digital infrastructure truly as robust as you believe? The reality is that inadequate SSH key management can expose your organization to devastating breaches, leaving you vulnerable to unauthorized access, data theft, and reputational damage. It's a threat lurking in the shadows of your systems, demanding immediate attention.
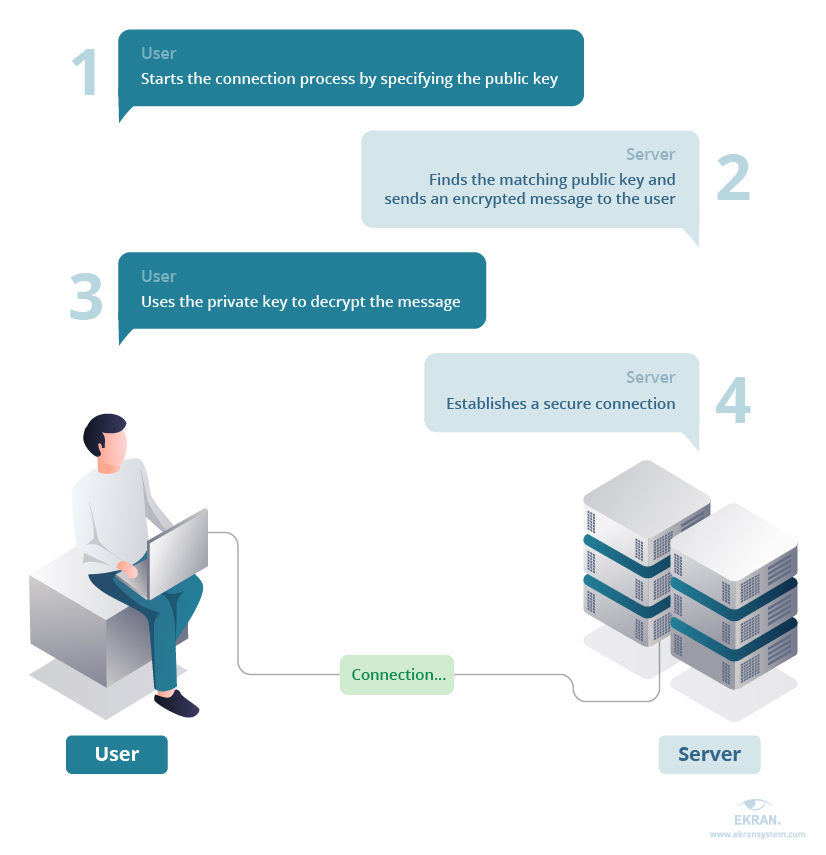
The digital landscape has transformed into a battleground, a constant clash of digital forces vying for control. Within this arena, the SSH key management system stands as a crucial, often overlooked, component of cybersecurity. It's the gatekeeper to servers, systems, and sensitive data, granting access to those with the proper credentials. However, if this gatekeeper is weak, misused, or poorly maintained, it becomes the perfect entry point for malicious actors. Consider the implications: a compromised SSH key could lead to a complete system takeover, the theft of critical intellectual property, or the disruption of essential business operations. Understanding the nuances of SSH key management is no longer optional; it's an imperative for any organization operating in today's interconnected world.
The complexities of SSH key management are often underestimated. The process involves the generation, storage, distribution, and revocation of cryptographic keys used for secure shell (SSH) access. While seemingly straightforward, the scale and dynamism of modern IT environments introduce numerous challenges. Organizations typically have hundreds, even thousands, of servers, each potentially requiring unique SSH keys. Managing this volume manually is a recipe for disaster. The risks include key sprawl, where unused or forgotten keys remain active, acting as open doors for attackers; key compromise, where keys are stolen or leaked, leading to unauthorized access; and a lack of visibility, making it difficult to track key usage and identify potential vulnerabilities. Ignoring these challenges is akin to leaving the front door of your business unlocked an invitation to disaster. The potential consequences, from financial losses to legal repercussions and irreversible damage to reputation, are simply too severe to ignore.
Consider, for example, a hypothetical scenario. A software development company, let's call them "InnovateTech," experiences a significant data breach. Investigators determine that the breach occurred due to a compromised SSH key. The key, belonging to a former employee, was never properly revoked after their departure. This oversight allowed an attacker to gain access to InnovateTech's internal systems, steal proprietary code, and potentially disrupt their customer services. The cost? Millions of dollars in lost revenue, a steep decline in investor confidence, and severe damage to the company's standing in the industry. This is a stark illustration of the real-world consequences of poor SSH key management.
The implementation of a robust SSH key management system is the cornerstone of proactive security. The benefits extend far beyond simply preventing breaches. They encompass improved operational efficiency, enhanced compliance, and strengthened overall security posture. By automating key lifecycle management, organizations can dramatically reduce the time and effort required to manage keys, freeing up IT staff to focus on more strategic tasks. Automation also minimizes the risk of human error, a significant factor in key-related incidents. Furthermore, a well-defined system provides the necessary controls to meet industry regulations and compliance requirements, such as those mandated by PCI DSS, HIPAA, and GDPR. The resulting enhanced security posture provides peace of mind, protects valuable assets, and contributes to a more resilient business.
A critical component of a robust SSH key management system is the automation of key lifecycle processes. This encompasses the automated generation, provisioning, rotation, and revocation of keys. The system should be able to automatically generate SSH keys based on predefined policies and procedures, ensuring that keys are generated with the appropriate cryptographic strength. Provisioning involves the secure distribution of keys to authorized users and systems, while rotation refers to the scheduled replacement of existing keys with new ones. Revocation is the process of invalidating compromised or unnecessary keys, preventing their use. The automation of these processes minimizes manual intervention, reduces the risk of errors, and streamlines key management operations.
Key rotation, in particular, is an essential security practice that often goes overlooked. Regularly rotating SSH keys, typically on a predetermined schedule, limits the potential damage from a compromised key. Even if an attacker obtains a key, its lifespan is limited, reducing the window of opportunity for malicious activities. Rotation also helps organizations to detect potential breaches more quickly. By monitoring key usage and identifying unusual activity, they can identify and respond to potential threats before they cause significant damage. The frequency of key rotation should be tailored to the specific security requirements of the environment, with more sensitive systems requiring more frequent rotations.
The cornerstone of an effective SSH key management system is its ability to provide comprehensive visibility into key usage. This involves detailed logging and auditing of all SSH key activities. The system should record information such as which keys are being used, when they were used, by whom, and for what purpose. This information is invaluable for identifying potential security incidents, tracing the source of a breach, and demonstrating compliance with regulatory requirements. Regular analysis of logs can reveal patterns of suspicious behavior, such as unauthorized access attempts or unusual key usage patterns, allowing security teams to take proactive measures to mitigate risks.
The selection of an appropriate SSH key management system should be guided by a careful assessment of the organization's specific needs and security requirements. Several factors should be considered, including the size and complexity of the IT environment, the sensitivity of the data being protected, and the existing security infrastructure. The system should integrate seamlessly with existing tools and technologies, and it should be scalable to accommodate future growth. Consider whether the system offers features such as centralized key storage, automated key rotation, access control policies, and robust logging and auditing capabilities. Prioritizing these elements ensures a comprehensive and effective security solution.
Centralized key storage is a critical component of a secure SSH key management system. Rather than storing keys on individual servers or user devices, a centralized repository allows for the secure storage and management of keys in a single location. This approach simplifies key lifecycle management, reduces the risk of key sprawl, and improves overall security. The centralized repository should employ strong encryption and access controls to protect keys from unauthorized access. In addition, the system should provide the ability to manage key permissions, allowing administrators to control which users or systems can access specific keys.
Another crucial aspect of SSH key management involves establishing robust access control policies. These policies define who can access specific resources and under what conditions. The system should provide the ability to enforce these policies automatically, restricting access to only authorized users and systems. Access control policies can be based on various factors, such as user roles, network location, time of day, and the specific resources being accessed. Integrating with existing authentication and authorization systems, such as Active Directory or LDAP, can streamline access control and reduce administrative overhead. Regularly reviewing and updating access control policies is also essential to ensure they remain effective in a dynamic environment.
Choosing a solution that offers features such as automated key rotation, centralized key storage, and access control policies is pivotal. A well-designed system also integrates logging and auditing for thorough tracking of key usage and security events. It's a matter of evaluating the specifics of your needs and security landscape. A system should seamlessly integrate with existing technologies, be scalable for future growth, and offer centralized key storage, automated key rotation, and robust logging and auditing to protect your infrastructure effectively.
It is vital that you do not underestimate the significance of employee training and awareness programs. No matter how sophisticated your security measures, they will be compromised if your employees lack the necessary knowledge and understanding to follow best practices. Educate employees about the importance of strong passwords, safe key handling practices, and the potential risks of phishing attacks. Regularly update training materials to reflect the latest threats and security best practices. Fostering a security-conscious culture within the organization is essential to mitigating risks and protecting the integrity of the system.
Continuous monitoring and assessment of the SSH key management system are essential. Security threats evolve constantly, and vulnerabilities can emerge over time. Regular vulnerability scans and penetration testing can identify weaknesses in the system, allowing you to take corrective measures before they are exploited. Monitoring SSH key usage patterns can help detect anomalous activity that could indicate a breach. Stay informed about the latest security threats and vulnerabilities, and adapt your key management practices accordingly. By continually evaluating and improving your SSH key management practices, you can ensure that your organization remains resilient against evolving threats.
The benefits of an effective SSH key management system extend beyond enhanced security. The streamlining of administrative operations is another key advantage. Manual key management is time-consuming and prone to errors. Automating key lifecycle processes, such as key generation, provisioning, rotation, and revocation, frees up IT staff to focus on more strategic tasks. By reducing manual intervention, you also minimize the risk of human error and improve overall efficiency. This allows for better resource allocation, improved operational productivity, and cost savings over the long term.
Compliance is not just about adhering to regulations; it's about establishing trust and demonstrating commitment to protecting sensitive data. Regulatory compliance, such as PCI DSS, HIPAA, and GDPR, requires organizations to implement robust security controls, including secure SSH key management. A well-designed system provides the necessary controls to meet these requirements, allowing you to demonstrate compliance to auditors and regulators. By complying with regulations, organizations can avoid costly fines, protect their reputation, and build trust with customers and stakeholders.
Implementing an SSH key management system is not a one-time task; it's an ongoing process. Continuous monitoring and evaluation are essential to ensure the system remains effective. Regular reviews of key usage patterns, security logs, and access control policies are necessary to identify and address potential vulnerabilities. Stay informed about the latest security threats and best practices, and adapt your key management practices accordingly. By taking a proactive approach to SSH key management, you can build a more secure, compliant, and efficient IT infrastructure. It's a continuous journey of vigilance and improvement, guaranteeing your organization remains fortified against the ever-evolving digital threats.
In the ever-evolving cybersecurity landscape, prioritizing strong SSH key management is no longer optional; it is an essential necessity. The consequences of neglecting this critical aspect of security are far too severe to ignore. By implementing a robust SSH key management system, you can strengthen your defenses, safeguard valuable assets, and cultivate a more secure and resilient digital environment. Take immediate action to protect your organization and secure your future in the ever-changing digital world.