Are you struggling to access your Raspberry Pi remotely, hampered by the complexities of firewalls and network configurations? The ability to securely and effortlessly connect to your Raspberry Pi, regardless of its location, is no longer a distant dream, but a readily achievable reality.
The challenge of remotely accessing a Raspberry Pi often stems from firewalls, which act as gatekeepers, preventing unauthorized access to your device. Standard methods, such as port forwarding, can be cumbersome and may expose your device to security risks. This guide will delve into various techniques, emphasizing security and ease of use, to ensure you can connect to your Raspberry Pi from anywhere in the world.
First, let's examine the fundamental concept of SSH (Secure Shell). SSH is a cryptographic network protocol that allows you to establish a secure connection to a remote server, in this case, your Raspberry Pi. It provides a secure channel for managing and interacting with your device remotely, offering a command-line interface for executing commands, transferring files, and more. Understanding SSH is paramount to remotely accessing your Raspberry Pi securely.
One of the most basic methods involves port forwarding. If your Raspberry Pi runs an SSH server on port 22 (the default), and you configure your router to forward external port 40022 to the internal port 22 of your Raspberry Pi, you can connect to your Pi from outside the network using port 40022. However, this approach can introduce security vulnerabilities. This is because you are essentially opening a direct path to your device, making it susceptible to potential attacks. As a result, it's crucial to implement robust security measures, such as strong passwords and, preferably, key-based authentication, to mitigate these risks.
To enable SSH remote access on your Raspberry Pi, you typically execute a specific command. The exact command may vary depending on your Raspberry Pi's operating system (usually Raspberry Pi OS, which is based on Debian). Often, SSH is enabled by default. If not, you can usually enable it through the Raspberry Pi configuration tool or by using a command-line interface. It's always a good idea to verify that SSH is enabled before attempting a remote connection. Further, changing the default SSH port from 22 to a different port is considered a good security practice to minimize the risk of automated attacks.
For a more secure and often more convenient method, consider using a reverse SSH tunnel. This technique is particularly useful when you are behind a firewall that restricts incoming connections. Instead of opening a port on your router, the Raspberry Pi initiates an outbound connection to an external server. This connection creates a tunnel, allowing you to connect back to your Raspberry Pi through the external server. This approach is considered secure because it does not require you to open any ports on your router. The Raspberry Pi initiates the connection, and the external server acts as an intermediary.
A Virtual Private Network (VPN) offers another highly effective solution. A VPN creates a secure, encrypted tunnel between your local device and your Raspberry Pi. This allows you to bypass the firewall and access your Raspberry Pi as if you were on the same local network. VPNs are generally considered very secure, as they encrypt all traffic between your device and the Raspberry Pi. Setting up a VPN, however, can require some technical expertise, but the benefits in terms of security and ease of access are well worth the effort.
Consider the scenario: youre trying to SSH into a remote server with key-based authentication, but you encounter a "connection refused" error. You've set up port forwarding, designating external port 1522 to forward to your Raspberry Pi's internal port 22. This error message suggests that the connection is being blocked, either by your router's firewall, the Raspberry Pi's own firewall, or perhaps the SSH server is not running or is configured incorrectly. Troubleshooting these issues is essential. Check your router's settings to ensure the port forwarding rule is correctly configured. On your Raspberry Pi, verify that the SSH server is active and listening on the correct port. And lastly, make sure your firewall rules are not interfering with the connection.
It's important to remember that, as of Mon Jan 20, 2025, 4:00 pm, network configurations and best practices for accessing your Raspberry Pi remotely are constantly evolving. Staying current with the latest security recommendations and software updates is critical to maintaining a secure connection.
One of the challenges that Raspberry Pi users face is the need to access their devices remotely, especially when those devices are behind firewalls, or have frequently changing IP addresses. The ability to access your Raspberry Pi remotely is important for many reasons. It enables you to monitor your devices from anywhere, troubleshoot problems, and install software. It allows you to use your Raspberry Pi as a home automation hub, a media server, or for other tasks that require remote access.
For instance, if your Raspberry Pis IP address changes (due to being on a different network), the previously working remote access setup would cease to function. This often happens when the Raspberry Pi is moved to another location with a different router and ISP. A dynamic DNS service could resolve this, but it's not always the ideal solution.
The Raspberry Pi ecosystem offers a wide array of software options. The Raspberry Pi OS is a dedicated operating system. It provides a user-friendly desktop environment, compatible with various peripherals. Many applications are available including desktop environments for PC and Mac. Other systems like Android, Debian, FreeBSD, Gentoo, Linux Kernel, NetBSD, OpenSUSE, Plan 9, Puppy, Arch, and Pidora are also supported, providing various flexibility in how the user interacts with the device.
When setting up remote access, security should be your primary concern. The goal is to establish a seamless and secure connection. Therefore, it's crucial to implement the right tools, make proper configurations, and know how to troubleshoot any problems. For example, use strong passwords and regularly update your operating system and software to patch any known vulnerabilities. Furthermore, setting up fail2ban to block suspicious activity can significantly improve your security posture.
Port forwarding is an essential aspect of remote access, but it needs to be done correctly. In your router's settings, you create a new port forwarding rule. This rule tells the router to forward incoming traffic on a specific external port to the internal IP address and port of your Raspberry Pi. You can give the rule a descriptive name, like "Raspberry Pi SSH". This is typically the same as the external port that you choose. For example, if you select 2222 as your external port, you would use that value in the port forwarding rule. The other common option, and considered a good security practice, is to choose an unusual port, such as 40022. This is done to reduce the chances of a successful attack. The Raspberry Pi itself must also be configured to listen to the port that has been configured.
Once the port forwarding is correctly set up, you can use an SSH client (such as PuTTY on Windows or the built-in terminal on macOS and Linux) to connect to your Raspberry Pi remotely. You will need the public IP address of your router (which you can find by searching "what is my IP" on the internet), and the external port you configured. For example, you might connect using ssh user@your.public.ip.address -p 40022.
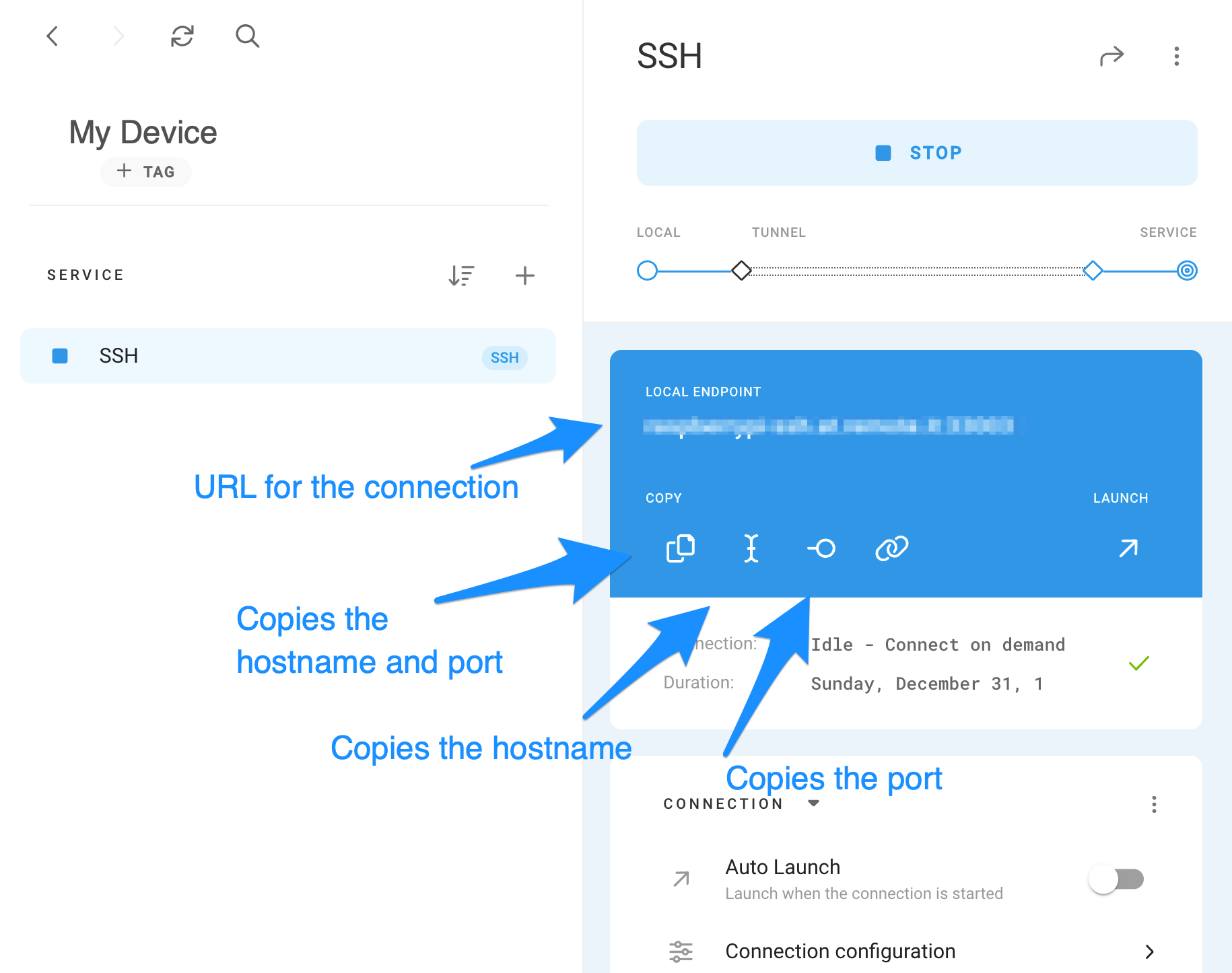
Several platforms offer secure remote access solutions. Services like remoteiot and SocketXP IoT remote access provide ways to skip the hassles of manual configurations. They often involve setting up an account, installing an agent on your Raspberry Pi, and then connecting through a secure cloud platform. These services typically provide a hostname and port that you can use to connect to your Raspberry Pi. The main benefit of such services is that they often work without requiring you to configure port forwarding or VPNs.
Another method to consider is using a VPN, which provides a secure tunnel between your local device and your Raspberry Pi. VPNs create a secure, encrypted connection, bypassing the firewall and allowing you to access your Raspberry Pi as if you were on the same local network. VPNs are generally considered very secure, as they encrypt all traffic between your device and the Raspberry Pi. Setting up a VPN, however, can require some technical expertise, but the benefits in terms of security and ease of access are well worth the effort.
Tailscale is a more specialized VPN solution. It simplifies setting up a VPN by utilizing a mesh network. It creates a secure tunnel that is easy to configure and can bypass many firewall issues. Tailscale simplifies the process by using a mesh network, making it easy to establish secure connections without the complexities of traditional VPN setups. It works by creating a secure network overlay, allowing devices to communicate directly with each other, no matter where they are located. This eliminates the need for complex port forwarding configurations. It is easy to set up and use, and it works well with Raspberry Pi devices.
Using a service like Cloudflare tunnels is another excellent option. Cloudflare tunnels provide a secure way to access your Raspberry Pi outside your home network. Cloudflare tunnels work by creating a secure, outbound connection from your Raspberry Pi to the Cloudflare network. This outbound connection makes it easier to access your Raspberry Pi because you don't need to configure port forwarding.
To install Samba on your Raspberry Pi, run the following command, which installs all the dependencies you need to run a Samba server or client. Accessing files on a network can be done using Samba. It allows you to create network shares. Raspberry Pi OS does not include Samba, so it needs to be installed.
Accessing your Raspberry Pi remotely is about more than just convenience; its about efficiency. It enables you to manage and interact with your device without being physically present. As a developer or hobbyist, remote access allows you to work on your projects from anywhere. The process can be achieved using various methods: SSH, VNC, or RDP. Choosing the right method depends on your specific needs and the security requirements.
For Raspberry Pi users, SSH offers a convenient way to manage and interact with their device without being physically present. SSH offers a secure and powerful method for remote access and management of your Raspberry Pi. It's a foundational tool for anyone working with Raspberry Pi devices remotely.
To achieve this remotely, security is of paramount importance. To ensure secure and reliable connections, it's important to follow best practices, which includes using strong passwords and keeping your software updated. Also, consider using key-based authentication rather than password-based authentication for improved security. This makes it more difficult for malicious actors to gain unauthorized access to your device.
Here is a table summarizing the various methods discussed for remotely accessing your Raspberry Pi:
| Method | Description | Pros | Cons | Security Considerations |
|---|---|---|---|---|
| Port Forwarding | Configuring your router to forward external ports to your Raspberry Pi's internal IP address and port. | Simple to set up. | Requires configuring your router, can expose your Pi to the internet if not set up securely. | Use strong passwords, change default SSH port, and consider key-based authentication. |
| Reverse SSH Tunnel | Establishing an outbound connection from your Raspberry Pi to an external server. | Bypasses firewall restrictions, relatively secure. | Requires an external server, slightly more complex to set up. | Ensure the external server is trustworthy. |
| VPN (Virtual Private Network) | Creating an encrypted tunnel between your device and your Raspberry Pi. | Highly secure, allows access as if on the local network. | Requires VPN configuration, can be more complex. | Choose a reputable VPN provider. |
| Cloudflare Tunnels/ Remote IoT Platforms | Using a service to create an outbound connection and provide a secure access point. | Easy to set up, often bypass firewall and NAT issues. | Requires trusting the service provider. | Review service provider's security practices. |
One of the most important and efficient steps is to protect against threats through Fail2Ban. The tool monitors your log files for malicious activities such as failed login attempts. If it detects such patterns, it automatically bans the offending IP addresses, making your system more resistant to brute-force attacks. This proactive approach significantly enhances the security of your Raspberry Pi.
The Remote SSH Raspberry Pi behind firewall solutions have become increasingly important for users managing their devices remotely. These methods offer flexible and secure access. With the methods outlined above, you can confidently connect to your Raspberry Pi, no matter where you are located, even when behind a firewall.
You can SSH, VNC, or RDP into your Raspberry Pi remotely over the internet. Many of the solutions described in this article are free to use, making remote access feasible for everyone. Before accessing remotely, ensure that your Raspberry Pi is connected to the internet, and the SSH server is enabled.
Remember, whether you're a developer, a hobbyist, or someone who simply enjoys tinkering with technology, the ability to remotely access your Raspberry Pi can dramatically enhance your productivity and enjoyment of the device. By mastering the techniques outlined in this guide, you'll be well-equipped to manage your Raspberry Pi from anywhere in the world.